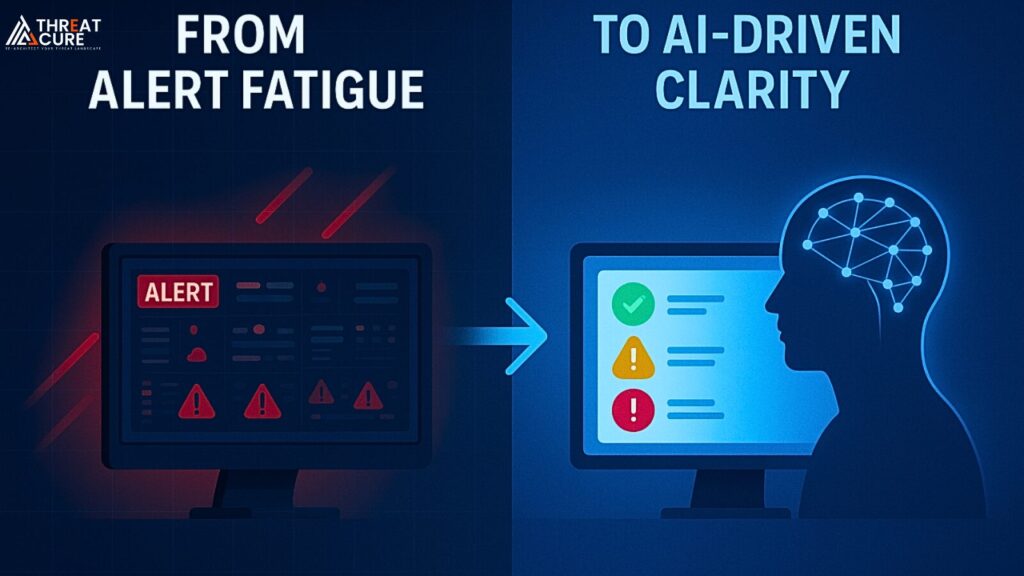
Redefining the SOC: From Manual Triage to AI-Driven Defense
have relied heavily on analysts manually triaging alerts, monitoring multiple dashboards, and dealing with a flood of false positives. This approach is becoming increasingly difficult to sustain. The pace and scale of today’s threats demand a more adaptive model.AI is now reshaping SOC operations in three important ways:1. Noise Reduction – Filtering False Positives That […]
Redefining the SOC: From Manual Triage to AI-Driven Defense Read More »